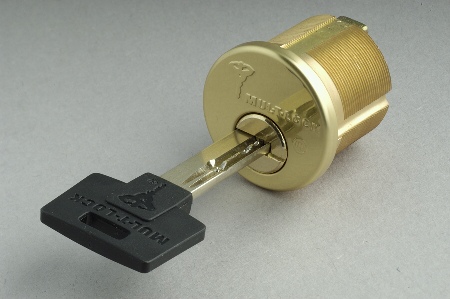
Figure 1. A Mul-T-Lock cylinder .
8 May 2003
(updated 20 May 2005 and 26 May 2005)

Figure 1. A Mul-T-Lock cylinder .
Mul-T-Lock is an internationally distributed line of high security lock cylinders distinguished by the use of a telescoping "pin-within-a pin" tumbler design and horizontally-oriented "dimple" keys. The locks are UL-listed and are hardened against forceful attack. Most cylinders have 5 tumblers. Each tumbler contains an inner and an outer pin, giving a total of 10 independently keyed elements in a 5 tumbler lock. (There are also versions that include additional secondary security elements, including side pins; they are not shown here.)

Figure 2. Mul-T-Lock cylinder face
Mul-T-Lock keyways are are oriented horizontally in the plug. Keys are double sided as a user convenience and can be inserted either way, although only the top of the key actually interacts with the pins. Note the front-most pin visible under the two right wards (at the center of the plug) in Figure 2.

Figure 3. Mul-T-Lock key bitting.
Mul-T-Lock keys resemble "dimple" type keys, although the individual bittings are drilled as two concentric rings, one for the outer pin and another for the inner.

Figure 4. Telescoping Mul-T-Lock pin stack.

Figure 5. Telescoping Mul-T-Lock pin stack (exploded).
Top pins (top of Figures 4 and 5) contain an internal spring that pushes down the inner top pin; the outer pin is held down by a conventional spring (not shown). The inner and outer bottom pins are held down by the inner and outer upper pins, respectively. The inner bottom pin has a slight spool top that prevents it from passing out the end of the outer bottom pin. Master keying is done in the obvious way, with additional pin segments.
A variety of security pin arrangements are used. Some early models do not use any special security pins (except the inner bottom pin spool), but more recent samples use serrated top outer pins (as shown here). Occasionally, mushroom bottom outer pins are used as well. There do not appear to be any special security pins used for the inner top pins, at least in the (limited) samples I have examined.
How secure are these locks? They are at least as secure against force as any other UL-listed cylinder, incorporating hardened pins or ball bearings over drill points and other potentially vulnerable spots. Key control is probably above-average, at least with respect to unauthorized commercial duplication. Blanks are restricted to contractually-authorized dealers, and the keys cannot be cut on conventional low-cost equipment. However, a moderately skilled machinist would likely have relatively little trouble producing counterfeit keys or blanks.
The keyspace is sufficiently large to make key interchange unlikely, with ten different keyed elements and no MACS between tumblers (although there may be MACS restrictions between the inner and outer cuts of a given tumbler).
Resistance to conventional picking is good, especially in cylinders that incorporate serrated and mushroom pins (but see below). However, note that because of the telescoping pin arrangement, defeating any of these cylinders is more akin to picking two five pin locks in sequence than one ten pin lock. The outer pins can be picked first, which allows the plug to turn a few degrees, which then allows the inner pins to be picked separately. With properly adapted picking tools, this is not especially difficult (on cylinders without security pins). The locks also appear to be vulnerable to vibration and snap-gun picking, although conventional commercial tools made for this purpose do not fit properly in the keyway. Impressioning might also be possible, although this would require access to blanks and special cutting equipment (a conventional fine metal file would probably not suffice). Foil impressioning may be feasible, but is complicated by the small space between inner and outer pins.
Michaud's attack exploits the arrangement of the springs that hold down the inner and outer pins of each tumbler. Recall that the spring for the "inner" pin stack is contained entirely within the top pin assembly, while the spring for the "outer" pin stack is a conventional-style spring that sits above the entire tumbler within its pin chamber in the cylinder shell. Because the smaller inner spring is weaker and more easily compressed than the "outer" spring, in ordinary operation upward pressure on the inner pin is entirely absorbed by the inner spring and does not cause the outer upper pin to move at all. That is, the design is intended to make the inner and outer pin stacks move independently of one another. Unfortunately, this may not actually be the case, and it appears to be possible to use one pin stack to manipulate the other.
In particular, observe that once the inner spring is fully compressed (e.g. by over-lifting the inner bottom pin), any further lifting of the inner pin transmits directly to the top pin assembly itself. That is, once the inner pin has been raised enough to fully compress the inner spring, the outer top pin itself begins to move, and will eventually rise above the shear line. However, because no motion is transmitted to the bottom outer pin at all, the bottom outer pin does not move as the inner pin is raised. Therefore, over-lifting the bottom inner pin beyond the point at which the inner spring is fully compressed eventually creates a gap in the outer pin stack at the shear line. If all inner pins are simultaneously over-lifted in this way, the plug can be rotated slightly, trapping the outer top pin assemblies above the shear line.
Michaud's attack, then, consists of three stages. First, a special tool is inserted into the plug that over-lifts all (typically five) inner pins and the plug rotated as described. Next, the tool is withdrawn with the plug held in position, such that the outer top pin assemblies remain trapped above the shear line but the inner pins do not bind. At this point the inner pin stacks can fall back to their normal resting position (with the bottom inner pin segment below the shear line and the top inner pin segment crossing the shear line). Finally, stronger torque is applied to rotate the plug, which binds the upper inner pins. This allows the inner pins to be raised to the shear line one by one, much as in conventional lock picking. However, because of the angle at which the inner upper pins are trapped, this should be a much simpler task than ordinary lock picking. In particular, the inner pins can apparently be set in any order (or simultaneously); they all bind at once and over-setting is prevented by the severe angle at which the upper pins are held.
The main tool required for this attack is a small "comb" with small wire probes that fit the inner pin of each pin stack. The tool must be constructed so that it does not lift the outer bottom pins above the shear line once inserted or while being removed. (These pins can be lifted during insertion, however, since torque is not applied until after the tool is in place). Such a tool is not commercially produced, but should be relatively simple to fabricate from commonly available materials (such as music wire).
Aside from its practical significance, Michaud's attack is interesting because it illustrates an ironic, and yet surprisingly common, failure mode in security engineering: the exploitation of one security subsystem to defeat another. The individual components of the pin-within-a-pin mechanism are very well designed and Mul-T-Lock's fabrication is of very high quality. But because the inner pins interact subtly (and in unanticipated ways) with the outer pins, it might be simpler to attack the "high security" design than it would be if the features were not included in the first place.
|
26 May 2005 update: Ron Rachlin, President of Mul-T-Lock
USA, expressed skepticism as to whether current versions of the
telescoping tumblers make it possible to over-lift an inner pin
without rotating the plug enough to engage the anti-picking (e.g.,
spool and serration) features and thereby jamming one or more pins.
He points out that Mul-T-Lock's latest products include more of these
features in the top-inner pins than those shown in the 2003 photos
above. (I must admit to not fully sharing his skepticism here,
however, since Michaud's attack does not apply any torque while the
tool is being inserted in the cylinder and the inner pins lifted.
However, it is certainly true that any anti-pick features make it
especially important that the plug be held sufficiently still during
the over-lifting stage of the attack to allow the pins to move
freely.)
Perhaps most significantly, Mr. Rachlin noted that some cylinders, particularly those deployed in master keyed systems, are not populated entirely with telescoping pin tumblers but include ordinary-style "solid" pins in some of the chambers. The Michaud attack would not be effective against cylinders keyed in this manner, since inner-pin-based over-lifting must be able to be performed on all tumblers simultaneously. (This is perhaps the only instance of which I am aware in which master keying actually improves, rather than degrades, security!) That said, none of the three samples I purchased at retail in 2003 in New York City included such pins, nor did Michaud report encountering any in the cylinders he purchased in 2004 in New Jersey. Given this, it is possible that the latest-production versions of Mul-T-Lock cylinders resist Michaud's attack, although it was unclear to me from our conversation whether cylinders aimed at the retail market (e.g., those intended for non-mastered commercial and residential use) are now routinely combinated with at least one solid pin. (Such a practice, if followed, would constitute an effective countermeasure, albeit at the expense of part of the keyspace). |
Images taken with a Nikon D-100 digital camera with a Nikkor
85mm 1:2.8D tilt/shift macro lens (with Kenko extension tube).
Lit by electronic flash and various reflectors.
All images and text Copyright © by Matt Blaze. All rights reserved. You may not copy, modify or use these images or text, in whole or in part, for any commercial or non-commercial purpose without permission.
8 May 2003; revised 20 May 2005